Generate Rsa Key Pair Openssl
- Generate Rsa Key Pair Openssl 1
- Generate Rsa Public Private Key Pair Openssl
- Generate Rsa Key Pair Openssl Number
Mar 03, 2020 You can generate a 2048-bit RSA key pair with the following commands: openssl genpkey -algorithm RSA -out rsaprivate.pem -pkeyopt rsakeygenbits:2048 openssl rsa -in rsaprivate.pem -pubout -out rsapublic.pem These commands create the following public/private key pair: rsaprivate.pem: The private key that must be securely stored on the.
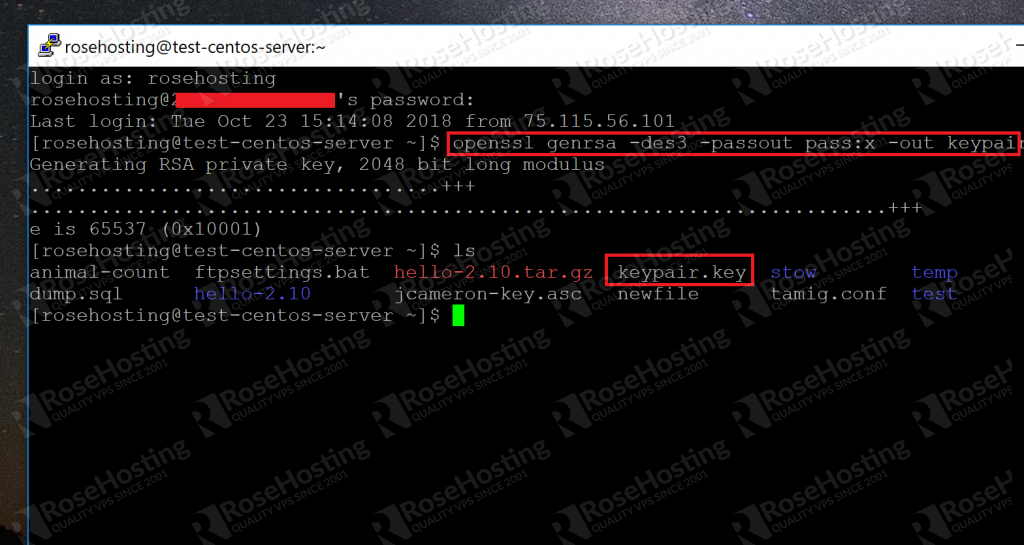
To execute the following commands, you will need an OpenSSL runtime installed (which you can download and install from the OpenSSL website, or install one from your operating system’s package management system). Generate an RSA key pair with a 2048 bit private key, by executing the following command: 'openssl genrsa - out privatekey.pem 2048'. To generate a key pair, select the bit length of your key pair and click Generate key pair. Depending on length, your browser may take a long time to generate the key pair. A 1024-bit key will usually be ready instantly, while a 4096-bit key may take up to several minutes. For a faster and more secure method, see Do It Yourself below. OpenSSL can generate several kinds of public/private keypairs. RSA is the most common kind of keypair generation. Other popular ways of generating RSA public key / private key pairs. I am trying to generate RSA 1024 key pair (public/private) using the following command openssl genrsa -des3 -out server.key 1024 In the server.key file, only RSA private block is there, so where. Generating the Private Key - Linux 1. Open the Terminal. Navigate to the folder with the ListManager directory. Type the following: openssl genrsa -out rsa.private 1024 4. The private key is generated and saved in a file named 'rsa.private' located in the same folder. Generating the Public Key - Linux 1. Open the Terminal.
You need to programmatically create a public/private key pair using the RSA algorithm with a minimumkey strength of 2048 bits. Vsphere 6.5 license key generator. The method you use to generate this key pair may differ depending onplatform and programming language.
Generating a public/private key pair by using OpenSSL library
The steps below are an example of the process for generating a public/private key pair for key exchange,using OpenSSL. To execute the following commands, you will need an OpenSSL runtime installed (whichyou can download and install from the OpenSSL website, or install one from your operating system’spackage management system).
- Generate an RSA key pair with a 2048 bit private key, by executing the following command:
'openssl genrsa - out private_key.pem 2048'
The following sample shows the command: - Extract the public key from the RSA key pair, by executing the following command:
'openssl rsa -pubout -in private_key.pem -out public_key.pem'
The following sample shows the command:A new file, public_key.pem , is created with the public key.
- Follow the instructions in the next (Validating your private key) section to confirm that your key meets the required criteria.
Validating your private key
When a private key has been generated, you can use the following OpenSSL command to verify that theprivate key fits the required criteria.
- Execute the following command:
'openssl rsa -in private_key_sample.pem -text' - Verify that the first line of the output includes the private key strength:
Private Key: (2048 bit)
If the first line of output states “ unable to load Private Key ,” your private key is not a valid RSA private key.
How to generate keys in PEM formatusing the OpenSSL command line tools?
RSA keys
The JOSE standard recommends a minimum RSA key size of 2048 bits.
To generate a 2048-bit RSA private + public key pair for use in RSxxx and PSxxxsignatures:
Elliptic Curve keys
To generate an EC key pair the curve designation must be specified. Note thatJOSE ESxxx signatures require P-256, P-384 and P-521 curves (see theircorresponding OpenSSL identifiers below).
Generate Rsa Key Pair Openssl 1
Elliptic Curve private + public key pair for use with ES256 signatures:
Elliptic Curve private + public key pair for use with ES384 signatures:
Elliptic Curve private + public key pair for use with ES512 signatures:
PEM key parsing in Java
Generate Rsa Public Private Key Pair Openssl
The BouncyCastle library provides a simpleutility to parse PEM-encoded keys in Java, to use them for JWS or JWE later.
For Maven you should include the following BouncyCastle dependencies (where1.52 is the latest stable version as of May 2015):
Generate Rsa Key Pair Openssl Number
Example parsing of an PEM-encoded EC key in Java: