Generate A New Key For File Valut 2
Purpose: How to create a Private Key, CSR and Import Certificate on Microsoft Azure KeyVault (Cloud HSM)
Requirements
1. You must have an active Microsoft Azure account.
2. You must have selected either the Free or HSM (paid) subscription option. These steps will work for either Microsoft Azure account type.
3. Microsoft Azure PowerShell must be installed. You can download it here.
The solution is in three parts:
1) Login and Create a Resource Group
2) Creating a Private Key and Certificate Signing Request (CSR)
3) Importing the Public Signed Certificate to Microsoft Azure KeyVault
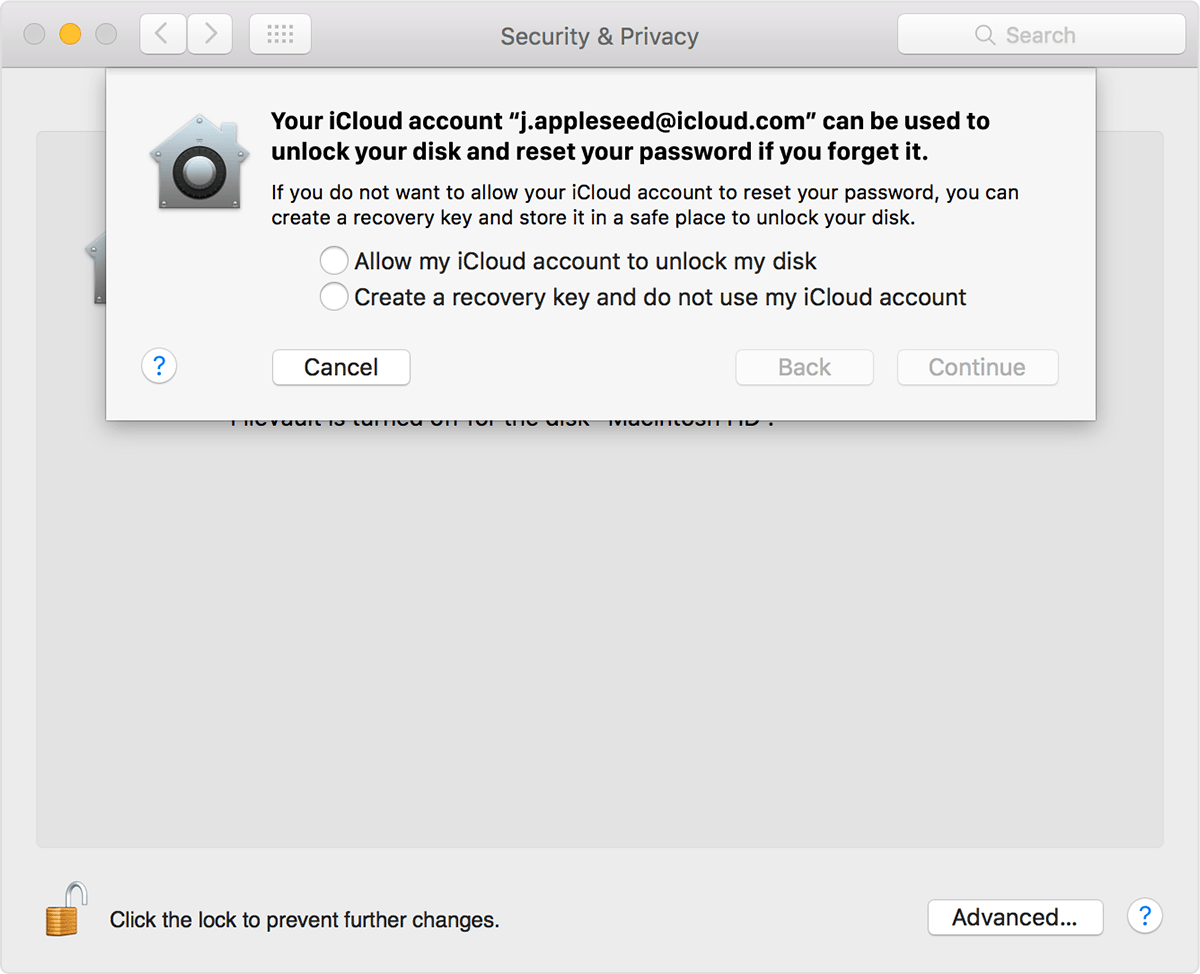
- Should I Turn On Filevault
- Generate A New Key For Filevault 2 Full
- Generate A New Key For File Valut 2017
1. Launch Microsoft Azure PowerShell.
2. Log in to your Microsoft Azure account by typing:
Login-AzureRmAccount
You will be prompted to enter your credentials to log in to your account. Once you login successfully you will see something like the below:
3. Determine your Resource Group. If you already have an existing Resource Group, you can skip this step. Otherwise, to create a resource group you need to provide the pieces of information shown below:
| Entity | Description | Example |
| Resource Group Name | This is the name you choose for your Resource Group. | ECSTestCertificatesGroup |
| Location | Geographic location for your key. | Canada Central |
To create a new resource group, use the command below:
New-AzureRMResourceGroup -Name 'ECSTestCertificatesGroup' -Location 'Canada Central'
4. Determine your keyvault. If you do not have an existing keyvault, you will need to generate one.
To create a new keyvault follow the command line below:
New-AzureRmKeyVault -VaultName '<your Vault Name>' -ResourceGroupName '<your Group Name>' -Location '<your Location>' -SKU 'Premium'
Where:
You can issue a new FileVault 2 recovery key to computers with OS X v10.9–v10.11 that have FileVault 2 activated. This allows you to do the following: Update the recovery key on computers on a regular schedule, without needing to decrypt and then re-encrypt the computers. I have been trying to create a class which has a property for key value pair, I have tried the Dictionary keyword, but I need something like this: ClassName clsName = new ClassName; clsName.PropertyName.Add'Key' = value; I want it to be dynamic property so I can send any datatype. The FileVault option in macOS is a fantastic way to enhance the security of your data at rest. It’s full-disk encryption (FDE), meaning that your entire startup volume is locked away when macOS is shut down (not just sleeping) using strong encryption. This parameter is required when you create a new key. If you import a key by using the KeyFilePath parameter, this parameter is optional: If you do not specify this parameter, and this cmdlet imports a key that has.byok file name extension, it imports that key as an HSM-protected key. The cmdlet cannot import that key as software-protected key.
| Entity | Description | Example |
| VaultName | Your own Vault Name. This name is unique. Microsoft Azure will reject your Vault Name if someone else has already registered that name in the Cloud. | MyNewECSKeyVault |
| ResourceGroupName | Your own Group Name (chosen in Step 3). | ECSTestCertificatesGroup |
| Location | Geographic location for your key. | Central Canada |
1. Make sure you are still logged into your Microsoft Azure account from PowerShell.
2. Set the parameters for your certificate policy by using the following commands:
$vaultName = '<your Vault Name>'
$certificateName = '<your Certificate Name>'
$manualPolicy = New-AzureKeyVaultCertificatePolicy -SubjectName '<your FQDN>' -ValidityInMonths 24 -IssuerName Unknown
Where:
| Entity | Description | Example |
| $vaultName | Your Vault Name. | MyNewECSKeyVault |
| $CertificateName | Your own designated Certificate Friendly Name. | MyCSCertificate |
| -subjectName | Your Fully Qualified Domain Name (FQDN). | CN=www.testcertificates.com |
3. Execute the Certificate Operation Command:
$certificateOperation = Add-AzureKeyVaultCertificate -VaultName $vaultName -Name $certificateName -CertificatePolicy $manualPolicy
Your private key has been generated. To view your private key inside KeyVault, use the command:
Get-AzureKeyVaultKey -VaultName 'MyNewECSKeyVault'
4. Generate Certificate Signing Request (CSR) by using the below command:
$certificateOperation.CertificateSigningRequest
You have successfully created the CSR and are ready to create the certificate. This is the CSR you will use to create the certificate in either your ECS Enterprise Account or during the ordering process if you are requesting an individual Code Signing certificate.
After completing the creation of your certificate using either your ECS Enterprise account, or by completing the individual certificate purchase on our website, follow these steps to successfully import the Public Signed Certificate to Microsoft Azure KeyVault:
1. Download your certificate, which will be delivered in a .zip format.
2. Unzip the file and store it to your local drive so you may import it to Microsoft Azure Keyvault.
3. Import the certificate to Microsoft Azure KeyVault using the command:
Import-AzureKeyVaultCertificate -VaultName $vaultName -Name $certificateName -FilePath
Where:
| Entity | Description | Example |
| $VaultName | Your Vault Name. | MyNewECSKeyVault |
| $CertificateName | Your Certificate Friendly Name | MyCSCertificate |
| FilePath | Location in your drive where you store your downloaded certificate file. | C:azuretestServerCertificate.crt |
You have successfully imported your certificate into your Microsoft Azure KeyVault Cloud HSM.
Note that at this time Microsoft Azure does not allow direct signing from within keyvault. Applications that use a keyvault must authenticate by using a token from Azure Active Directory. That means the usage of keyvault is limited to Azure Cloud environment only and cannot be used for third party application outside this realm. For more information, see this article by Microsoft.
For best practices regarding the protection of private keys related to Code Signing certificates, please see our Best Practices article here.
If you have any questions or concerns please contact the Entrust Certificate Services Support department for further assistance:
Hours of Operation:
Sunday 8:00 PM ET to Friday 8:00 PM ET
North America (toll free): 1-866-267-9297
Outside North America: 1-613-270-2680 (or see the list below)
NOTE: It is very important that international callers dial the UITF format exactly as indicated. Do not dial an extra '1' before the '800' or your call will not be accepted as an UITF toll free call.
| Country | Number |
| Australia | 0011 - 800-3687-7863 1-800-767-513 |
| Austria | 00 - 800-3687-7863 |
| Belgium | 00 - 800-3687-7863 |
| Denmark | 00 - 800-3687-7863 |
| Finland | 990 - 800-3687-7863 (Telecom Finland) 00 - 800-3687-7863 (Finnet) |
| France | 00 - 800-3687-7863 |
| Germany | 00 - 800-3687-7863 |
| Hong Kong | 001 - 800-3687-7863 (Voice) 002 - 800-3687-7863 (Fax) |
| Ireland | 00 - 800-3687-7863 |
| Israel | 014 - 800-3687-7863 |
| Italy | 00 - 800-3687-7863 |
| Japan | 001 - 800-3687-7863 (KDD) 004 - 800-3687-7863 (ITJ) 0061 - 800-3687-7863 (IDC) |
| Korea | 001 - 800-3687-7863 (Korea Telecom) 002 - 800-3687-7863 (Dacom) |
| Malaysia | 00 - 800-3687-7863 |
| Netherlands | 00 - 800-3687-7863 |
| New Zealand | 00 - 800-3687-7863 0800-4413101 |
| Norway | 00 - 800-3687-7863 |
| Singapore | 001 - 800-3687-7863 |
| Spain | 00 - 800-3687-7863 |
| Sweden | 00 - 800-3687-7863 (Telia) 00 - 800-3687-7863 (Tele2) |
| Switzerland | 00 - 800-3687-7863 |
| Taiwan | 00 - 800-3687-7863 |
| United Kingdom | 00 - 800-3687-7863 0800 121 6078 +44 (0) 118 953 3088 |
Creates a new key, stores it, then returns key parameters and attributes to the client.
The create key operation can be used to create any key type in Azure Key Vault. If the named key already exists, Azure Key Vault creates a new version of the key. It requires the keys/create permission.
URI Parameters
| Name | In | Required | Type | Description |
|---|---|---|---|---|
| path | True |
| The name for the new key. The system will generate the version name for the new key. Regex pattern: | |
vaultBaseUrl | path | True |
| The vault name, for example https://myvault.vault.azure.net. |
| query | True |
| Client API version. |
Request Body
| Name | Required | Type | Description |
|---|---|---|---|
| attributes | The attributes of a key managed by the key vault service. | ||
| crv | Elliptic curve name. For valid values, see JsonWebKeyCurveName. | ||
| key_ops |
| JSON web key operations. For more information, see JsonWebKeyOperation. | |
| key_size |
| The key size in bits. For example: 2048, 3072, or 4096 for RSA. | |
| kty | True | The type of key to create. For valid values, see JsonWebKeyType. | |
| tags |
| Application specific metadata in the form of key-value pairs. |
Responses
| Name | Type | Description |
|---|---|---|
| 200 OK | A key bundle containing the result of the create key request. | |
| Other Status Codes | Key Vault error response describing why the operation failed. |
Examples
Create key
Sample Request
Definitions
| DeletionRecoveryLevel | Reflects the deletion recovery level currently in effect for keys in the current vault. If it contains 'Purgeable' the key can be permanently deleted by a privileged user; otherwise, only the system can purge the key, at the end of the retention interval. |
| Error | The key vault server error. |
| JsonWebKey | As of http://tools.ietf.org/html/draft-ietf-jose-json-web-key-18 |
| JsonWebKeyCurveName | Elliptic curve name. For valid values, see JsonWebKeyCurveName. |
| JsonWebKeyType | JsonWebKey Key Type (kty), as defined in https://tools.ietf.org/html/draft-ietf-jose-json-web-algorithms-40. |
| KeyAttributes | The attributes of a key managed by the key vault service. |
| KeyBundle | A KeyBundle consisting of a WebKey plus its attributes. |
| KeyCreateParameters | The key create parameters. |
| KeyVaultError | The key vault error exception. |
DeletionRecoveryLevel
Reflects the deletion recovery level currently in effect for keys in the current vault. If it contains 'Purgeable' the key can be permanently deleted by a privileged user; otherwise, only the system can purge the key, at the end of the retention interval.
| Name | Type | Description |
|---|---|---|
| Purgeable |
| |
| Recoverable |
| |
| Recoverable+ProtectedSubscription |
| |
| Recoverable+Purgeable |
|

Error
The key vault server error.
| Name | Type | Description |
|---|---|---|
| code |
| The error code. |
| innererror | The key vault server error. | |
| message |
| The error message. |
JsonWebKey
As of http://tools.ietf.org/html/draft-ietf-jose-json-web-key-18
| Name | Type | Description |
|---|---|---|
| crv | Elliptic curve name. For valid values, see JsonWebKeyCurveName. | |
| d |
| RSA private exponent, or the D component of an EC private key. |
| dp |
| RSA private key parameter. |
| dq |
| RSA private key parameter. |
| e |
| RSA public exponent. |
| k |
| Symmetric key. |
| key_hsm |
| HSM Token, used with 'Bring Your Own Key'. |
| key_ops |
| Supported key operations. |
| kid |
| Minitool power data recovery 8.1 key generator. Key identifier. |
| kty | JsonWebKey Key Type (kty), as defined in https://tools.ietf.org/html/draft-ietf-jose-json-web-algorithms-40. | |
| n |
| RSA modulus. |
| p |
| RSA secret prime. |
| q |
| RSA secret prime, with p < q. |
| qi |
| RSA private key parameter. |
| x |
| X component of an EC public key. |
| y |
| Y component of an EC public key. |
JsonWebKeyCurveName
Elliptic curve name. For valid values, see JsonWebKeyCurveName.
| Name | Type | Description |
|---|---|---|
| P-256 |
| The NIST P-256 elliptic curve, AKA SECG curve SECP256R1. |
| P-256K |
| The SECG SECP256K1 elliptic curve. |
| P-384 |
| The NIST P-384 elliptic curve, AKA SECG curve SECP384R1. |
| P-521 |
| The NIST P-521 elliptic curve, AKA SECG curve SECP521R1. |
JsonWebKeyType
JsonWebKey Key Type (kty), as defined in https://tools.ietf.org/html/draft-ietf-jose-json-web-algorithms-40.
| Name | Type | Description |
|---|---|---|
| EC |
| Elliptic Curve. |
| EC-HSM |
| Elliptic Curve with a private key which is not exportable from the HSM. |
| RSA |
| RSA (https://tools.ietf.org/html/rfc3447) |
| RSA-HSM |
| RSA with a private key which is not exportable from the HSM. |
| oct |
| Octet sequence (used to represent symmetric keys) |
Should I Turn On Filevault
KeyAttributes
The attributes of a key managed by the key vault service.
| Name | Type | Description |
|---|---|---|
| created |
| Creation time in UTC. |
| enabled |
| Determines whether the object is enabled. |
| exp |
| Expiry date in UTC. |
| nbf |
| Not before date in UTC. |
| recoveryLevel | Reflects the deletion recovery level currently in effect for keys in the current vault. If it contains 'Purgeable' the key can be permanently deleted by a privileged user; otherwise, only the system can purge the key, at the end of the retention interval. | |
| updated |
| Last updated time in UTC. |
KeyBundle
A KeyBundle consisting of a WebKey plus its attributes.
| Name | Type | Description |
|---|---|---|
| attributes | The key management attributes. | |
| key | The Json web key. | |
| managed |
| True if the key's lifetime is managed by key vault. If this is a key backing a certificate, then managed will be true. |
| tags |
| Application specific metadata in the form of key-value pairs. |
KeyCreateParameters
The key create parameters.
Generate A New Key For Filevault 2 Full
| Name | Type | Description |
|---|---|---|
| attributes | The attributes of a key managed by the key vault service. | |
| crv | Elliptic curve name. For valid values, see JsonWebKeyCurveName. | |
| key_ops |
| JSON web key operations. For more information, see JsonWebKeyOperation. |
| key_size |
| The key size in bits. For example: 2048, 3072, or 4096 for RSA. |
| kty | The type of key to create. For valid values, see JsonWebKeyType. | |
| tags |
| Application specific metadata in the form of key-value pairs. |
KeyVaultError
The key vault error exception.
Generate A New Key For File Valut 2017
| Name | Type | Description |
|---|---|---|
| error | The key vault server error. |