Can I Generate A Public Key From A Private Key
The.pub file is your public key, and the other file is the corresponding private key. If you don’t have these files (or you don’t even have a.ssh directory), you can create them by running a program called ssh-keygen, which is provided with the SSH package on Linux/macOS systems and comes with Git for Windows. Jul 09, 2019 Public Key Infrastructure (PKI) security is about using two unique keys: the Public Key is encrypted within your SSL Certificate, while the Private Key is generated on your server and kept secret. All the information sent from a browser to a website server is encrypted with the Public Key, and gets decrypted on the server side with the Private Key. In the Number of bits in a generated key box, enter 2048. Click Generate to generate a public/private key pair. As the key is being generated, move the mouse around the blank area as directed. (Optional) Enter a passphrase for the private key in the Key passphrase box and reenter it in the Confirm passphrase box.
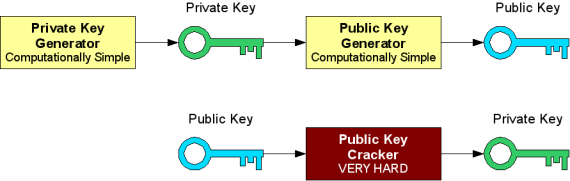
Lets say you have a private/public key pair that you use to login to your server via SSH and you lose the public key, either it was deleted or corrupt and you don’t want to have to regenerate a new pair what options do you have? In this post I will demonstrate how to regenerate a public key from the corresponding private key that you still have.
Generate public key and store into a file
Generate site key for google recaptcha. It is a simple one liner command to generate a public key from a private key, so lets say our private key is named ‘user@myserver.key’ and we want to generate the public key and name it ‘authorized_keys’. Below is the command to do this. Oracle vm virtualbox user manual rus.
‘> authorized_keys’: instead of printing the output to the console redirect the output (public key) to a file named ‘authorized_keys’
copy public key to your server
now we will need to take our authorized_keys file and store it on the server, if we can currently login via ssh to our server we can use rsync over ssh to securely copy the public key to the server, although this key is displayed to anyone who attempts to login to your server it is smart to use ssh or another secure method to copy it up to the server to ensure that the key is not tampered with while it is being transmitted.
below is an example using rsync to copy the authorized keys file to its destination on the server and removing it from your local computer.
‘> authorized_keys’: instead of printing the output to the console redirect the output (public key) to a file named ‘authorized_keys’
Copy public key to your server
Now we will need to take our authorized_keys file and store it on the server, if we can currently login via SSH to our server we can use rsync over ssh to securely copy the public key to the server, Although this key is displayed to anyone who attempts to login to your server it is smart to use SSH or another secure method to copy it up to the server to ensure that the key is not tampered with while it is being transmitted.
Below is an example using rsync to copy the authorized keys file to its destination on the server and removing it from your local computer.
‘> authorized_keys’: instead of printing the output to the console redirect the output (public key) to a file named ‘authorized_keys’
copy public key to your server
now we will need to take our authorized_keys file and store it on the server, if we can currently login via ssh to our server we can use rsync over ssh to securely copy the public key to the server, although this key is displayed to anyone who attempts to login to your server it is smart to use ssh or another secure method to copy it up to the server to ensure that the key is not tampered with while it is being transmitted.
below is an example using rsync to copy the authorized keys file to its destination on the server and removing it from your local computer.